Mutual Authentication in ServiceNow
In this article, I will give a high-level overview of what Mutual Authentication is, why we use it, and how it works.

Extract
In this article, I will give a high-level overview of what Mutual Authentication is, why we use it, and how it works.
I have used Mutual Authentication numerous times within ServiceNow and it is a very handy technology to learn and know especially if you find yourself integrating with a vast array of external technologies.
What is it?
Historically, authentication when it comes to web applications has been one-sided.
A consumer would use SSL to retrieve data from a provider and simultaneously confirm the authenticity of who the provider says they are using a chain of trust.
My SSL Certificate is this, and that's certified by someone up the chain, and that's certified by someone further up the chain, and on until you reach an overarching root source of trust.
Mutual Authentication takes this a step further and also verifies the authenticity of the consumer, this makes the authentication "two-way". A consumer confirms who the provider is and the provider confirms who the consumer is before any data is shared between the pair, somewhat like a handshake. Doing this allows both parties to know exactly who they are talking to before they start sharing secrets.
Why do we use it?
Mutual Authentication comes with many benefits, one of which is reduced security risks.
It eliminates the ability for bad actors to carry out certain types of attacks such as Man-in-the-Middle Attacks because the provider will not accept requests from attackers and the consumer will not accept spoofed responses from an attacker.
It also reduces or stops spoofing and impersonation attacks and also stops credential theft, when mutual authentication is set up using Certificates rather than passwords.
How does it work?
I will focus only on Certificate authentication in this article, however public key authentication as well as username and password methods also exist.
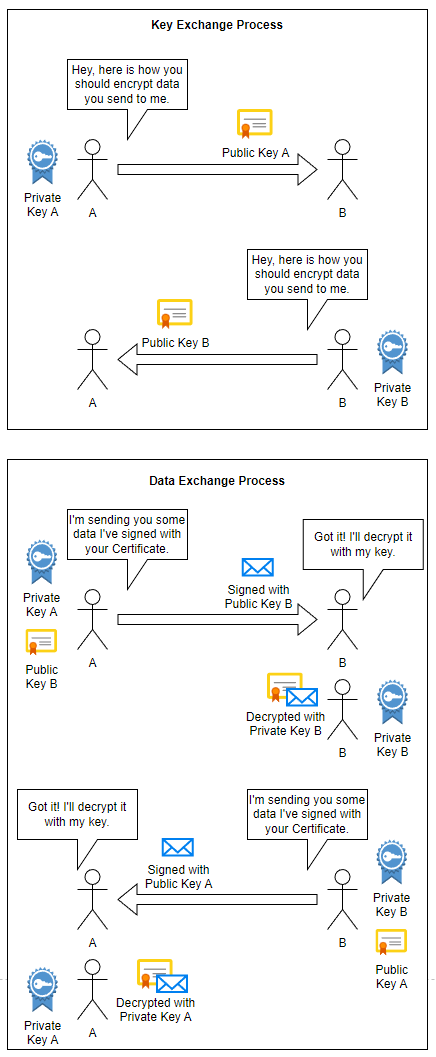
Key Exchange Process
Mutual Authentication starts with a Key Exchange process, essentially setting up the connection for later use. Consumer A has both a private and public key and Provider B has both a private and public key. Consumer A gives Provider B a copy of their public key and Provider B gives Consumer A a copy of their public key.
Data Exchange Process
When Consumer A wants to send data to Provider B, they encrypt the data using Provider B's public key, Provider B then decrypts this data using Provider B's private key and consumes the information.
When Provider B wants to send data to Consumer A, they encrypt the data using Consumer A's public key, Consumer A then decrypts this data using Consumer A's private key and consumes the information.
Mutual Authentication with ServiceNow
Below is a high level step by step process for enabling Mutual Authentication in ServiceNow.
Endeavouring not to recreate the wheel, I have highlighted the overall steps, but please see the attached links for detailed instructions.
Outbound
- Create a Key Store
- Set up Key Store record in ServiceNow
- Create a protocol profile
- Share the new Key Store's public key with your 3rd party web service provider
- Specify a Trusted Server Certificate
- Enable Mutual Authentication
Detailed instructions here: Configure Outbound Mutual Authentication (calling 3rd party Web Services) in ServiceNow Instance - Support and Troubleshooting
Inbound
- Activate Certificate-based authentication
- Register CA Certificate
- Map PEM certificate to user
Detailed instructions here: How to configure inbound Certificate Based Authentication (mutual authentication) in ServiceNow - Support and Troubleshooting
Closing
I hope this has given you a decent high level understanding of Mutual Authentication and how and why we use it and also the links required in order to set it up in ServiceNow should you wish to!
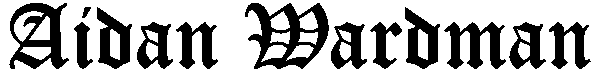




Comments ()